Network Security Monitoring Tools Top Picks

In today’s digital landscape, a cyberattack occurs every 39 seconds. That staggering statistic underscores a critical truth: protecting your network is no longer optional, it’s essential. Network Security Monitoring (NSM) tools are the vigilant guardians of your digital infrastructure, constantly observing network traffic for suspicious activity, policy violations, and potential security breaches.
But with a vast array of options available, choosing the right NSM solution can feel like navigating a minefield. This article aims to demystify the world of network security monitoring tools, providing you with a clear understanding of their capabilities, benefits, and the key factors to consider when selecting the best fit for your organization.
Prepare to learn how to proactively defend your network, detect threats in real-time, and ultimately, safeguard your valuable data from malicious actors.
Network Security Monitoring Tools: A Comprehensive Guide
In today’s connected world, keeping your digital assets safe is paramount. Network security monitoring (NSM) tools are the sentinels of your digital realm. They constantly watch network traffic, spotting unusual behavior and potential threats.
This guide dives into the realm of NSM tools, explaining what they are, why they matter, and how to choose the right ones. Get ready to level up your cybersecurity game and protect your valuable data.
Network Security Monitoring (NSM) tools are crucial for maintaining a secure digital environment. They operate as vigilant guardians, continuously observing network traffic and identifying irregularities that may indicate potential threats.
A strong NSM strategy allows you to proactively identify and address risks before they turn into significant security incidents. Implementing NSM is no longer an option but a necessity for any organization.
Why Network Security Monitoring Matters

Imagine your network as a city. NSM tools are the police force, watching for suspicious activities. They detect everything from malware infections to unauthorized access attempts, giving you time to react.
Without NSM, you’re essentially flying blind. You won’t know if a breach has occurred until it’s too late, and the damage is done. Think of lost data, financial losses, and reputational damage.
NSM goes beyond simple intrusion detection. It gathers comprehensive data about network activity, allowing for in-depth analysis and proactive threat hunting. This visibility is invaluable for improving your security posture.
Regular monitoring aids in identifying vulnerabilities and compliance gaps. You can proactively address these weaknesses, reducing your overall risk exposure. Staying ahead of threats requires a proactive approach.
Ultimately, effective NSM translates to improved resilience. You’ll be better equipped to withstand attacks, minimize damage, and recover quickly if a breach does occur. Business continuity is crucial.
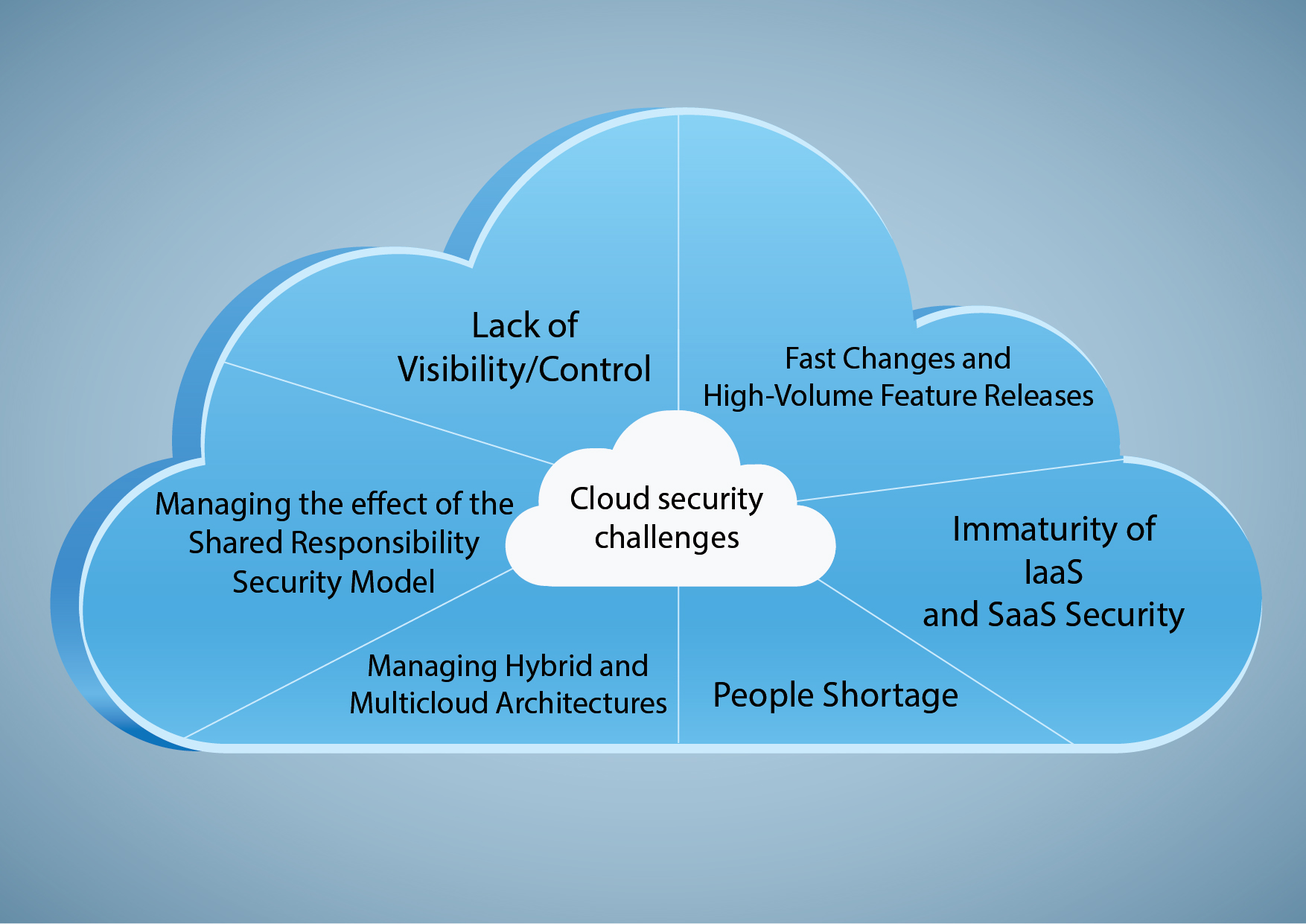
Types of Network Security Monitoring Tools
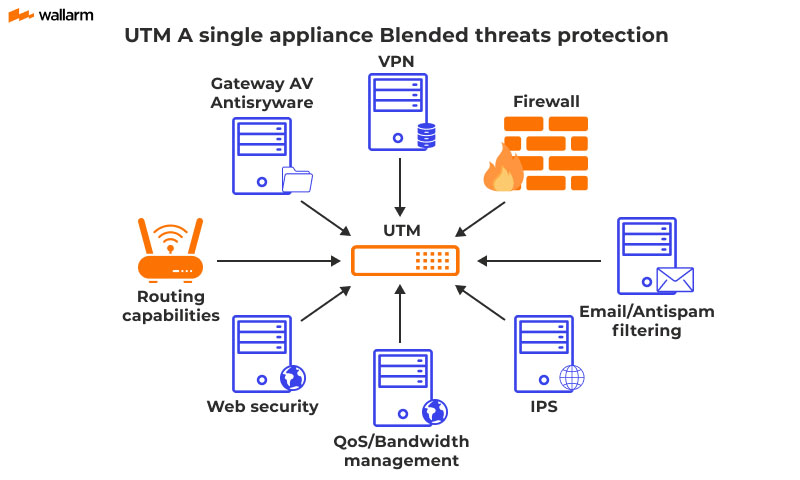
The NSM toolkit is diverse. Intrusion detection systems (IDS) look for known attack patterns. Security information and event management (SIEM) systems correlate logs from various sources to provide a holistic view.
Network traffic analysis (NTA) tools examine network packets to identify anomalies. Endpoint detection and response (EDR) solutions monitor individual devices for suspicious activity. Firewalls remain critical for perimeter defense.
Each tool serves a unique purpose, and the best approach is often a combination of several. Choosing the right tools depends on your specific needs, budget, and technical expertise.
Consider the size of your network, the sensitivity of your data, and the threats you’re most likely to face. A small business might need a different set of tools than a large enterprise. Tailoring your approach is key.
Open-source options can offer cost-effective alternatives, while commercial solutions often provide more advanced features and support. Evaluate all your options before making a decision. Consider long-term scalability as well.
Key Features to Look for in NSM Tools
When evaluating NSM tools, look for real-time monitoring capabilities. The sooner you detect a threat, the faster you can respond. Automated alerts are crucial for immediate notification.
Comprehensive logging and reporting features are essential for analysis and investigation. You need to be able to track activity over time and identify patterns. Detailed records are a must.
Integration with other security tools, such as firewalls and antivirus software, is crucial. A unified security ecosystem provides a more complete picture of your security posture. Synergy is paramount.
User-friendly interfaces and dashboards make it easier for security teams to manage and interpret the data. Simplicity is key for effective threat response. Intuitive design saves time and reduces errors.
Scalability is important to consider as your network grows. Choose tools that can handle increasing volumes of data and evolving threat landscapes. Future-proofing your security is a smart move.
Implementing Network Security Monitoring Effectively
Start with a clear understanding of your network architecture and critical assets. What are you trying to protect, and where are the biggest vulnerabilities? This understanding will guide your implementation strategy.
Develop well-defined security policies and procedures. These policies should outline what constitutes suspicious activity and how to respond to different types of threats. Clear guidelines are essential.
Train your security team on how to use the NSM tools and interpret the data. Proper training is essential for maximizing the value of your investment. Continuous learning is vital.
Regularly review and update your security policies and procedures. The threat landscape is constantly evolving, so your defenses must adapt as well. Stay vigilant and proactive.
Consider using a phased approach to implementation, starting with the most critical areas of your network. This allows you to refine your processes and avoid overwhelming your team. Incremental improvements are sustainable.
Popular Network Security Monitoring Tools
Several excellent NSM tools are available, each with its strengths and weaknesses. Suricata is a powerful open-source IDS/IPS engine. Zeek (formerly Bro) offers comprehensive network traffic analysis.
Snort is another widely used open-source IDS/IPS system. Wireshark is an excellent packet analyzer for troubleshooting and investigation. Security Onion is a Linux distribution specifically designed for NSM.
Commercial options include Splunk, which offers powerful SIEM capabilities. IBM QRadar is another popular SIEM platform. Darktrace uses AI to detect anomalous behavior in real-time.
The “best” tool depends on your specific requirements and resources. Research and compare different options before making a decision. Consider free trials and demos to test out various platforms.
Read reviews and case studies to see how other organizations are using these tools. Learn from the experiences of others to make an informed choice. Community feedback can be invaluable.