Cyber Security Audit Is Your Business Safe

In today’s interconnected world, a single data breach can cripple a business, costing not just money but also its reputation. Are you confident your organization is truly protected from evolving cyber threats? A cyber security audit is your organization’s health check, a comprehensive assessment of your existing security measures to identify vulnerabilities and ensure compliance with industry best practices.
It’s not just about ticking boxes; it’s about building a resilient defense against potential attacks. This article delves into the core of cyber security audits, explaining their purpose, the key components involved, and the benefits they provide.
By understanding the audit process, you can proactively strengthen your security posture, protect valuable data, and gain peace of mind knowing your organization is well-prepared for the challenges of the digital age. Learn how to implement effective audits and transform potential weaknesses into fortified strengths.
Understanding the Cyber Security Audit: Protecting Your Digital Assets
In today’s interconnected world, a robust cybersecurity posture is not merely a suggestion, but a necessity. A cybersecurity audit is a comprehensive assessment of your organization’s security measures.
It identifies vulnerabilities, assesses risks, and offers guidance on how to bolster your defenses against potential threats. This isn’t a one-time fix, but a continuous process of improvement.
The increasing sophistication of cyberattacks demands that businesses take a proactive approach. A well-executed audit is a crucial element in a solid cybersecurity strategy.
Think of it as a health checkup for your digital infrastructure. It helps you understand your weaknesses and gives you the tools to improve your overall security health.
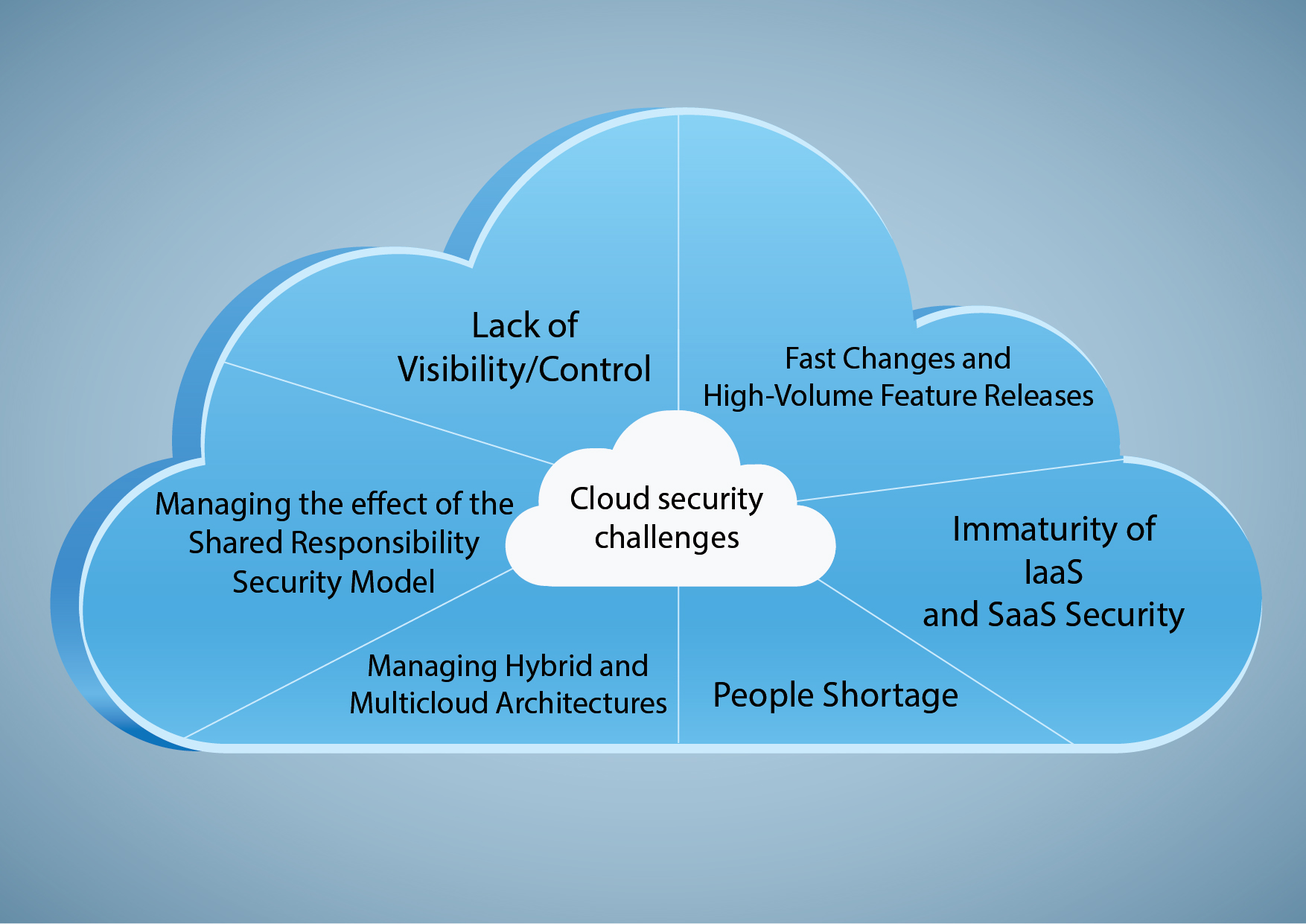
Why is a Cyber Security Audit Important?
The digital landscape is constantly shifting, and new threats emerge daily. An audit keeps you informed about evolving dangers. It gives your company awareness of possible breaches.
Compliance with regulations is also a vital aspect. Many industries have specific security requirements, and an audit ensures you meet them. Stay up-to-date with evolving rules.
Beyond regulations, a cyber security audit instills trust. It demonstrates to customers and stakeholders that you prioritize data protection. Build stronger relationships by showing your commitment.
It’s about more than just avoiding fines or negative press. It’s about building a culture of security within your organization. Security isn’t just IT’s job; it’s everyone’s responsibility.
Early detection of vulnerabilities helps prevent costly breaches and data losses. Investing in an audit is far more cost-effective than dealing with the aftermath of a successful attack.
Key Components of a Cyber Security Audit

A typical audit begins with a thorough review of your existing policies and procedures. Are your policies current, effective, and followed by all employees? Review the entire company from top to bottom.
Next, a vulnerability assessment identifies potential weaknesses in your systems. This involves scanning for known flaws and misconfigurations. Find where cracks can turn into holes.
Penetration testing takes it a step further. Ethical hackers attempt to exploit identified vulnerabilities to gauge the true impact of a breach. How deep can they actually get?
The audit will also analyze your access controls. Who has access to sensitive data, and is that access appropriate for their role? Secure the critical entry points to your data.
The analysis extends to your incident response plan. Do you have a clear plan in place for dealing with a security breach? Test it to ensure it functions as intended. You need a plan to react quickly.
Types of Cyber Security Audits
There are different types of audits, each focusing on specific aspects of cybersecurity. A risk assessment focuses on identifying and evaluating potential threats. Know what can hurt you.
A compliance audit verifies adherence to industry standards or regulations. PCI DSS, HIPAA, and GDPR are common examples. Stay aligned with regulatory requirments.
A technical audit dives deep into your IT infrastructure. It assesses the security of your network, servers, and applications. Strengthen the core of your IT operation.
A vendor risk management audit evaluates the security practices of your third-party vendors. You’re only as strong as your weakest link. Ensure your supply chain is secure.
The choice of audit depends on your organization’s specific needs and goals. Some will be more helpful than others, so focus on what your company needs most.
Implementing Recommendations from a Cyber Security Audit
The audit report provides a detailed list of findings and recommendations. Prioritize these based on their potential impact and the resources required for remediation. Tackle the biggest risks first.
Develop a plan to address each recommendation. This should include timelines, assigned responsibilities, and required resources. Put the plan into motion and track progress.
Implement necessary security controls, such as firewalls, intrusion detection systems, and multi-factor authentication. Deploy the tech to protect your assets.
Provide regular security awareness training to employees. Human error is a major cause of breaches. Educate your staff on best practices and phishing attempts.
Regularly monitor your systems for suspicious activity. Early detection is crucial for minimizing the impact of a breach. Stay alert to catch issues quickly.
Best Practices for a Successful Cyber Security Audit
Start by defining the scope of the audit. What systems and data will be included? Establish clear objectives to guide the process.
Engage experienced cybersecurity professionals to conduct the audit. Their expertise is essential for a thorough and accurate assessment. Utilize people who are familiar with this process.
Be transparent and cooperative with the auditors. Provide them with the information they need to do their job effectively. Open communication is key to a successful review.
Treat the audit as an opportunity for improvement, not as a fault-finding exercise. Focus on learning from the findings and strengthening your security posture. Approach this as a helpful process.
Regularly update your security policies and procedures based on the audit findings and the evolving threat landscape. Keep your defense tactics current.