Top Open Source Cybersecurity Tools Free

Imagine a world where cybersecurity isn’t a closely guarded secret, but a collaborative effort, a constantly evolving ecosystem fueled by shared knowledge. That’s the promise of open source cybersecurity tools. But what exactly are they? Simply put, these are freely available software solutions designed to protect systems and data, where the source code is accessible for anyone to view, modify, and distribute.
In today’s threat landscape, relying solely on proprietary solutions can feel like fighting a war with one arm tied behind your back. Open source tools offer transparency, customizability, and a vibrant community constantly improving defenses. This article will delve into the world of open source cybersecurity, exploring its key benefits, showcasing powerful examples, and providing guidance on how you can leverage these tools to strengthen your security posture, regardless of your technical expertise.
Unveiling the Power of Open Source Cybersecurity Tools
In today’s digital realm, shielding your assets from online adversaries is more critical than ever. The reliance on technology grows, which creates opportunity for cybercriminals and malicious entities.
Luckily, there’s a vibrant community dedicated to crafting powerful defenses. They leverage the power of collaboration, and transparency through open source cybersecurity solutions.
Let’s explore these invaluable tools and see how they can enhance your protective stance. We will also cover how they can help businesses and individuals fortify their online defenses.
Understanding these tools is a step in the direction of a more protected digital lifestyle. It allows people to make informed decisions on the security measures they implement.
Why Choose Open Source for Cybersecurity?

Open source tools are publicly available, meaning anyone can look at the code that makes it up. This allows for independent scrutiny and verification of security and function.
Unlike proprietary software, you’re not locked into a single vendor. Open source fosters a community of developers who constantly improve and update the tools.
Often, open source options are more cost-effective. Businesses and individuals can access enterprise-grade protection. There is also the added flexibility of adapting the software to meet their needs.
Beyond the cost advantage, open source security tools provide unmatched customizability. Organizations can tweak software to adapt it to their unique circumstances and infrastructure.
Key Categories of Open Source Cybersecurity Tools
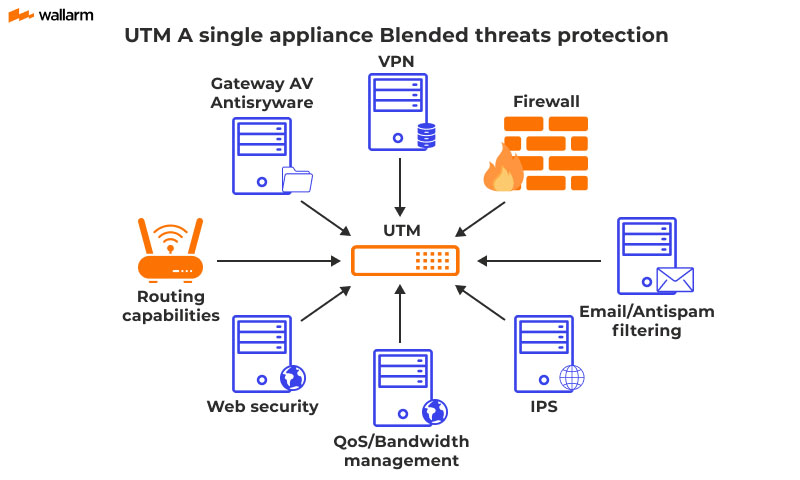
Network security is the backbone of any defense strategy. There are many programs available such as firewalls, intrusion detection systems, and network monitoring solutions to analyze network activity.
Vulnerability scanners are essential for proactively locating gaps in systems. They check for weaknesses before attackers can exploit them, allowing patching and mitigation.
Security information and event management (SIEM) systems are critical for managing threats. SIEM is a centralized platform for collecting, analyzing, and responding to security alerts across all systems.
Incident response platforms play a crucial role in mitigating damages after attacks. Such platforms provide tools to coordinate investigations, contain breaches, and recover systems rapidly.
Spotlight on Specific Open Source Cybersecurity Tools
Snort: A ubiquitous network intrusion detection system. It analyzes network traffic for suspicious activity and potential exploits.
Nmap: A powerful network scanner used to discover hosts and services on a network. It can be used to build a network “map.”
Wireshark: An amazing network protocol analyzer. It allows in-depth inspection of network traffic, helping with troubleshooting and threat analysis.
Metasploit: It’s not strictly a defensive tool, but rather a pentesting platform. It is used to simulate real-world attacks to validate defenses and pinpoint vulnerabilities.
Implementing Open Source Cybersecurity Tools
Begin by understanding your specific security requirements. Identify the vulnerabilities you need to address and the threats you must defend against.
Many open source tools require technical expertise to configure and manage. You can seek outside vendors to help manage your infrastructure.
Continuously monitor your systems and networks to detect any anomalies or suspicious activity. Regularly update your tools to ensure you have the latest security patches and feature enhancements.
Remember, open source doesn’t mean “set it and forget it.” Actively test and refine your security policies and configurations to ensure they are effective. You may want to hire someone to pentest the system.
The Future of Open Source in Cybersecurity
The landscape of open source solutions is likely to witness increased adoption. This is partly due to their transparency, community support, and potential cost savings.
Expect more advanced features. This includes machine learning, artificial intelligence, and automation. These will streamline threat detection, analysis, and response workflows.
Organizations will continue to contribute to open source projects. They do this by sharing knowledge, resources, and expertise to enhance the ecosystem’s overall security posture.
As the complexity of cyber threats grows, so will the role of open source. The collaboration and innovation it fosters is the biggest key to staying ahead of the curve.