Checkpoint Cybersecurity
Imagine your network as a bustling city, and its sensitive data as precious cargo needing safe passage. Just as checkpoints ensure only authorized vehicles enter, checkpoint cybersecurity diligently guards your digital assets. But in today’s increasingly complex threat landscape, are these checkpoints as effective as we believe? This article dives deep into the world of checkpoint cybersecurity, exploring its vital role in protecting networks from unauthorized access and malicious attacks.
We’ll unpack the core principles of this security approach, examine the common challenges organizations face in implementing and maintaining effective checkpoints, and uncover strategies for optimizing their performance. Whether you’re a seasoned cybersecurity professional or simply curious about how to better safeguard your digital environment, this guide provides valuable insights into strengthening your defenses and ensuring your critical data remains secure.
Understanding Checkpoint Cybersecurity: A Comprehensive Guide
In today’s digital landscape, cybersecurity is paramount. Checkpoint is a significant player in this field. They offer solutions to protect networks, data, and endpoints from a wide array of threats.
From large enterprises to small businesses, the necessity for robust cybersecurity is universal. Checkpoint aims to provide that shield, mitigating risks and ensuring operational stability. They address diverse security challenges faced by modern organizations.
This article dives into the world of Checkpoint cybersecurity. We’ll break down their core offerings, explore their strengths, and discuss how they stack up in the competitive security market.
Let’s explore what makes Checkpoint a contender in digital protection. This is your starting point for understanding their ecosystem. We’ll also address considerations for organizations looking to bolster their defenses.
Checkpoint’s Core Security Solutions

Checkpoint offers a broad range of security solutions. These are designed to address various facets of cyber defense. Their primary areas of focus include network security, cloud security, and endpoint security.
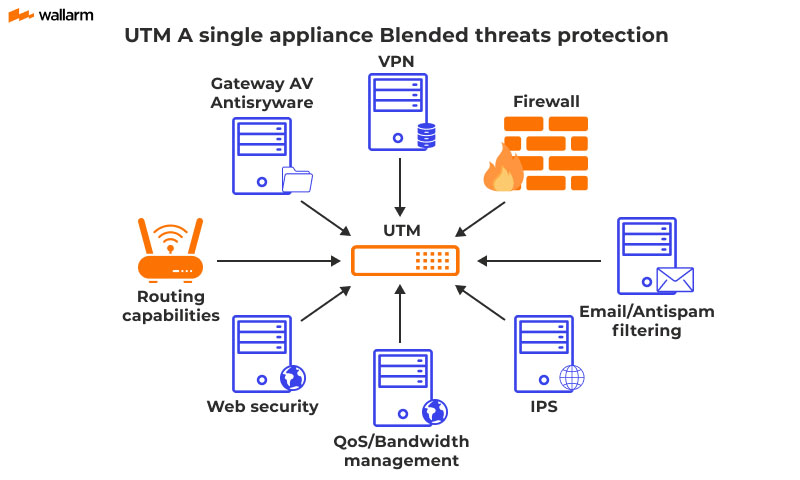
Network security is a cornerstone of Checkpoint’s portfolio. This encompasses firewalls, intrusion prevention systems (IPS), and virtual private networks (VPNs). They create secure channels and protect against outside access.
Cloud security is also a major offering. Checkpoint provides solutions that safeguard cloud environments. They ensure data protection and maintain regulatory compliance across public, private, and hybrid clouds.
Endpoint security rounds out their core offerings. These tools protect devices like laptops and desktops. They detect malware, prevent data loss, and control access to sensitive information.
Beyond these core areas, Checkpoint also provides threat intelligence services, security management tools, and solutions for mobile security. They really do aim to be a one-stop shop!
Key Features and Benefits of Checkpoint
Checkpoint’s products are known for their advanced threat prevention capabilities. Their solutions often incorporate features like sandboxing and behavioral analysis. These help identify and block zero-day exploits.
Another key benefit is their centralized management platform. This allows security teams to easily monitor and manage their security infrastructure from a single console, simplifying operations.
Scalability is also a strength. Checkpoint’s solutions can be scaled to meet the needs of growing businesses. This includes everything from a small startup to a large multinational corporation.
Checkpoint is known for its commitment to innovation and research. They continuously update their products to address the latest threats. This ensures ongoing protection against evolving cyberattacks.
They often integrate with other security tools and platforms. This provides a more holistic and coordinated security posture. This makes it easier to fold into existing security workflows.
Checkpoint vs. the Competition: What Sets Them Apart?
The cybersecurity market is saturated. Checkpoint faces stiff competition from other vendors. These include Palo Alto Networks, Cisco, and Fortinet. Each has their own strengths.
One area where Checkpoint often excels is its focus on threat prevention. Their solutions are built to proactively block attacks. This stands in contrast to simply detecting and responding to them.
Another differentiator is their unified security architecture. This provides a more integrated and streamlined approach to security management. It’s a popular feature with those who prioritize ease of use.
However, some competitors may offer a wider range of specialized solutions. These could cater to niche industries or specific use cases. No one size fits all!
Ultimately, the best choice depends on the organization’s specific needs. A thorough evaluation of different vendors is crucial to finding the right fit.
Implementing and Managing Checkpoint Solutions
Successful implementation is critical for getting the most out of Checkpoint solutions. It often involves careful planning, configuration, and integration with existing infrastructure.
Proper training is essential for security teams. They need to understand how to use and manage Checkpoint’s products effectively. This includes staying up-to-date on the latest features and threat landscape.
Regular security audits and vulnerability assessments are also important. These help identify any weaknesses in the security posture. They also ensure that Checkpoint’s solutions are properly configured.
Ongoing monitoring and maintenance are crucial for detecting and responding to security incidents. Security teams should have clear incident response plans in place.
Consider engaging with Checkpoint’s professional services or a trusted partner for assistance. This can ensure a smooth and successful implementation process. It can also maintain a robust security posture over time.