Network Security Providers

In today’s interconnected world, a data breach occurs every 39 seconds. That’s a stark reminder of the ever-present threats lurking in the digital realm. But how do businesses, both large and small, protect themselves from these relentless attacks? The answer often lies with network security providers.
These specialized companies offer a suite of services designed to safeguard your critical data and infrastructure, acting as a vigilant shield against cybercriminals. Think of them as the digital bodyguards for your business, constantly monitoring your network, identifying vulnerabilities, and responding to threats before they cause significant damage.
This article delves into the crucial role network security providers play in maintaining a secure and resilient digital environment. We’ll explore the range of services they offer, the common challenges they address, and what to consider when choosing the right provider to safeguard your valuable assets, ensuring you can navigate the digital landscape with confidence.
Choosing the Right Network Security Provider: A Comprehensive Guide
Securing your network isn’t optional these days; it’s a necessity. With threats lurking around every digital corner, picking the ideal network security provider is crucial for business survival. But how do you navigate the crowded landscape of options?
This article cuts through the noise, offering practical insights to help you find a guardian for your digital assets. We’ll discuss what to look for, potential pitfalls, and ways to ensure you’re making a smart investment.
Think of your network as a castle, and these providers as the guards. You need strong, reliable, and adaptable guards to defend against modern-day attackers. Let’s get started on your quest for the right security partner.
The goal is complete protection, ensuring your data remains confidential and your business stays operational. By understanding the different types of providers, you can find one that best fits your specific needs and budget.
Understanding Your Network Security Needs

Before you even start searching for a provider, take a hard look at your current setup. What are your vulnerabilities? What data needs the tightest protection? A self-audit is the first step toward solid defense.
Assess the size and complexity of your network. A small business has different requirements compared to a large enterprise. Don’t overspend on features you won’t use or underspend on protection you critically need.
Compliance requirements also play a big role. If you handle sensitive customer data, standards like HIPAA or PCI DSS might dictate the level of security you require. Understand these before talking to anyone.
Consider future growth. Will your network expand? Your security solution needs to scale along with you. Choosing a provider with flexible options will save you headaches down the road. This foresight is key.
Think about the skills of your current IT team. Will they manage the security solution, or will you need full managed services? This decision will heavily influence the type of provider you choose and its associated costs.
Key Services Offered by Network Security Providers
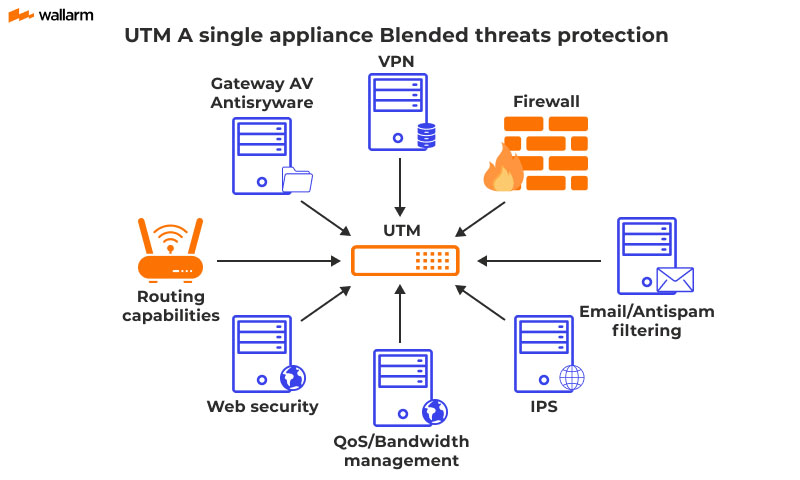
Network security providers offer a variety of services. Common options include firewalls, intrusion detection and prevention systems (IDS/IPS), VPNs, and endpoint security. But it’s not just about the tools; it’s how they’re implemented and managed.
Firewalls are your network’s first line of defense, controlling incoming and outgoing traffic. Choose a provider that offers next-generation firewalls with advanced threat intelligence for superior protection. Modern firewalls can adapt to threats.
IDS/IPS systems constantly monitor your network for suspicious activity. They detect and often automatically block threats, providing real-time security. Look for providers with strong threat intelligence feeds for optimal performance.
VPNs create secure tunnels for remote access to your network. This is essential for employees working from home or on the go. Select a provider that offers robust VPN solutions with strong encryption and multi-factor authentication.
Endpoint security protects individual devices like laptops and smartphones. This is especially vital in today’s BYOD (Bring Your Own Device) environments. Many providers offer comprehensive endpoint detection and response (EDR) solutions. Modern protection is important.
Evaluating Potential Providers: Questions to Ask
Once you have a shortlist of potential providers, it’s time to ask the tough questions. Don’t be afraid to dig deep and get specific. Their answers will reveal their capabilities and their commitment to your security.
Ask about their experience in your industry. A provider with a proven track record in your field will understand the specific threats you face and how to address them effectively. A specific history helps tremendously.
Inquire about their incident response plan. What happens if a breach occurs? How quickly can they respond? A well-defined incident response plan is critical for minimizing damage and restoring operations.
Ask about their security certifications and compliance adherence. Do they comply with relevant industry standards? This demonstrates their commitment to security best practices. Compliance is key to data security.
Find out about their monitoring and reporting capabilities. How often will they monitor your network? What kind of reports will they provide? You need visibility into your security posture to make informed decisions.
Don’t forget to ask about pricing and contract terms. Understand the total cost of ownership, including setup fees, maintenance, and support. Read the fine print carefully before signing anything. Avoid hidden fees.
Managed Security Services vs. In-House Solutions
You have two main choices: managed security services or building your own in-house solution. Managed services outsource your security to a third-party provider, while in-house solutions require dedicated staff and resources.
Managed services offer several advantages, including access to specialized expertise, 24/7 monitoring, and cost savings. They can be a great option for businesses that lack the resources to build a full-fledged security team. Expertise is key here.
In-house solutions give you more control over your security environment. However, they require significant investment in personnel, technology, and training. This option is best suited for larger enterprises with dedicated IT departments.
Consider the level of control you need and the resources you have available. Weigh the pros and cons of each approach carefully before making a decision. Control versus outsourcing: a common dilemma.
Hybrid models are also becoming increasingly popular. This approach combines managed services with in-house expertise, allowing you to leverage the strengths of both. It offers a balanced approach to security. It’s a good middle ground.
Staying Ahead of the Threat Landscape
The threat landscape is constantly evolving. New vulnerabilities and attack techniques emerge every day. It’s crucial to choose a provider that stays ahead of the curve and continuously adapts its security solutions.
Look for providers that invest in research and development and actively participate in threat intelligence sharing. This ensures they are aware of the latest threats and can proactively protect your network. Innovation is important.
Regular security assessments and penetration testing are essential for identifying vulnerabilities and weaknesses. Your provider should offer these services as part of its ongoing security program. Continuous assessment is needed.
Employee training is also critical. Human error is a major cause of security breaches. Train your employees to recognize phishing scams and other social engineering attacks. Users are a frequent vulnerability.
Review your security posture regularly. Don’t let your defenses become outdated. Adapt to new risks and emerging threats to stay one step ahead of the attackers. Never become complacent with security.