Application Network Security Is Your Data Safe
Did you know that a cyberattack occurs every 39 seconds? In today’s hyper-connected world, that staggering statistic underscores the critical importance of application and network security. But what exactly does this mean? Simply put, it’s the practice of safeguarding your software applications and the networks they rely on from malicious threats and unauthorized access.
Think of it as building a digital fortress around your valuable data and systems. This isn’t just a concern for large corporations; individuals and small businesses are equally vulnerable. This article delves into the world of application and network security, exploring common vulnerabilities, prevalent attack methods, and practical strategies you can implement to bolster your defenses.
We’ll unpack everything from robust authentication protocols to proactive monitoring techniques, empowering you to understand and address the ever-evolving landscape of digital threats and keep your digital assets safe and secure.
Application and Network Security: A Deep Dive
Navigating the digital world demands vigilance. Protecting sensitive data and ensuring seamless operations requires robust application and network security. Let’s explore the key facets of safeguarding your digital assets.
This article unpacks the core principles of application and network safety. We’ll explore common threats, proactive defense strategies, and best practices for maintaining a secure environment. Get ready to boost your understanding!
Think of it as fortifying your digital castle. With the right safeguards in place, you can ward off intruders, minimize risks, and establish a reliable foundation for growth. Ready to build a digital fortress?
From firewalls to encryption, a spectrum of techniques exists to combat various cyber dangers. We will discuss essential tools and tactics so you can protect your information from unauthorized access.
Understanding Application Security
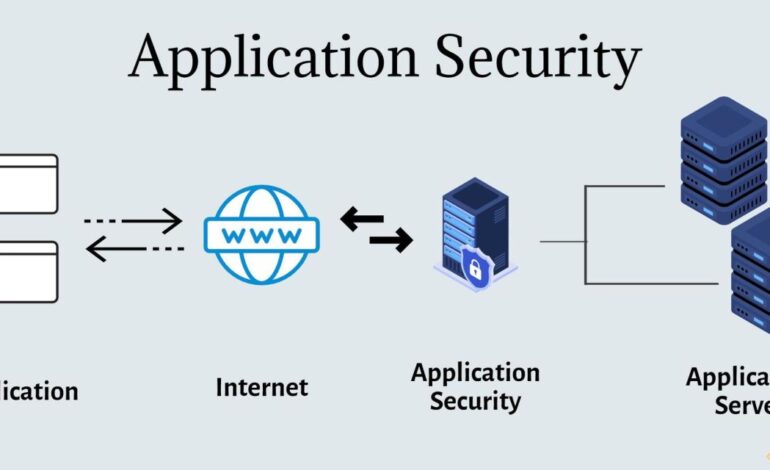
Application security focuses on protecting software from threats. This involves implementing security measures throughout the application development lifecycle. The goal is to prevent vulnerabilities.
Consider all the apps you use daily. Each one represents a potential entry point for attackers. Robust application safety practices act as a shield, defending your data and systems.
Several vulnerabilities can appear in applications. Input validation flaws, SQL injection, and cross-site scripting are just a few examples. Developers must be aware of these and take preventive steps.
It’s about more than just writing code. Safety requires ongoing testing, vigilant monitoring, and rapid response to emerging threats. A proactive approach is essential for long-term success.
Using secure coding practices is essential. Developers should follow security guidelines during every stage of the development process. It is a proactive measure.
Exploring Network Security
Network safety involves safeguarding your digital infrastructure. This includes protecting your network devices, data, and resources from unauthorized access and attacks. It is the first line of defense.
Think of your network as a highway system. Network safety measures act as traffic cops, regulating the flow of data and preventing malicious actors from causing accidents. Stay safe on the information superhighway!
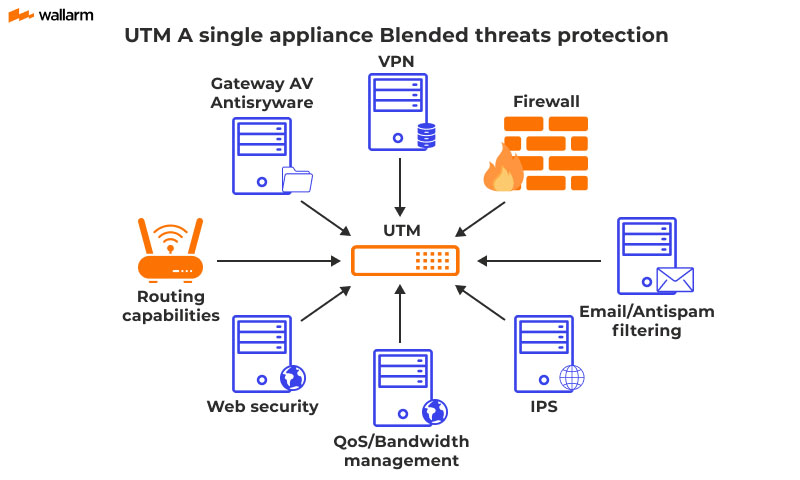
Firewalls, intrusion detection systems, and VPNs are crucial components. These technologies work together to monitor network traffic, block threats, and provide secure access for authorized users.
Effective network safety requires a layered approach. Multiple security controls work together to provide comprehensive protection. Think of it as having multiple layers of security screening.
Security professionals often perform penetration testing. These professionals actively attempt to exploit vulnerabilities in order to improve security configurations. It is important to monitor and update software and hardware for known vulnerabilities.
Common Application and Network Threats
Cyber threats are constantly evolving. Understanding the latest attack vectors is critical for maintaining robust safety. Awareness is the first step in defending against these evolving attacks.
Malware, including viruses and ransomware, remains a prevalent threat. These malicious programs can infiltrate your systems and cause significant damage. Preventative steps are necessary.
Phishing attacks trick users into revealing sensitive data. Attackers often use social engineering techniques to make their attacks more convincing. Education is the best defense.
Denial-of-service (DoS) attacks overwhelm systems with traffic. This makes them unavailable to legitimate users. These attacks can disrupt business operations and cause significant downtime.
Zero-day exploits take advantage of unknown vulnerabilities. These attacks occur before a patch is available. Defense requires proactive threat detection and rapid response capabilities.
Best Practices for a Secure Environment
Maintaining a secure environment requires continuous effort. Implementing best practices across your organization is essential. Security is a continuous process, not a one-time fix.
Regularly update your software and systems. Patches often contain critical safety fixes. Failure to update can leave you vulnerable to known exploits.
Implement strong access control measures. Limit user access to only the resources they need. This reduces the risk of unauthorized access and data breaches.
Educate employees about safety best practices. This can significantly reduce the risk of phishing attacks and other social engineering attempts. A well-trained workforce is your best asset.
Conduct regular security audits and assessments. This helps identify vulnerabilities and weaknesses in your environment. Knowledge is power when it comes to safety.
Use Multi-Factor Authentication. This will require additional authentication methods that are only known to the user, and can help prevent against brute force attacks and credential-based attacks.
The Future of Application and Network Security
The safety landscape is constantly evolving. New technologies and attack methods emerge regularly. Staying ahead of the curve requires continuous learning and adaptation.
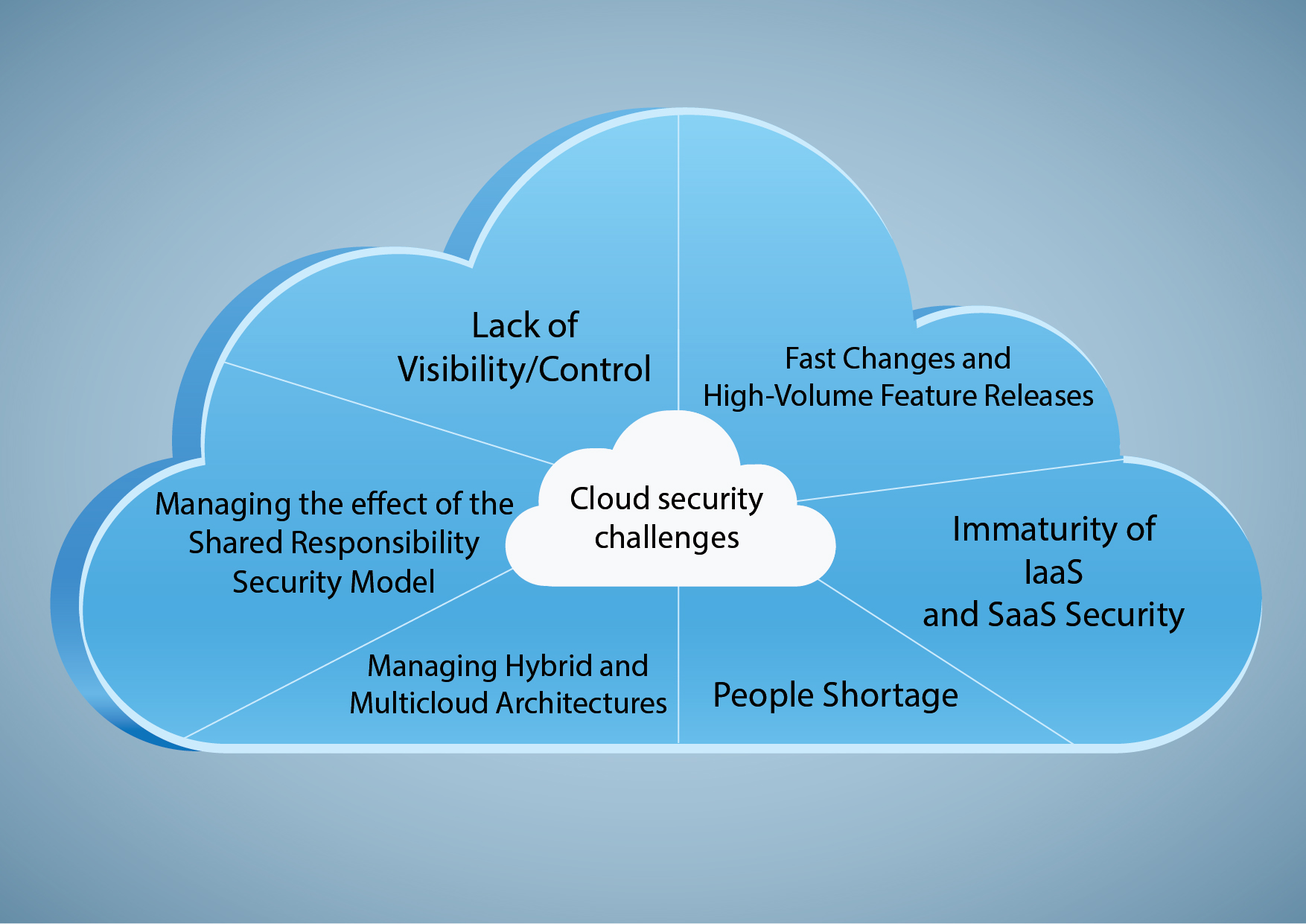
Cloud computing is transforming how applications and networks are deployed. This requires new safety approaches. Cloud security is becoming an increasingly important area of focus.
Artificial intelligence (AI) is playing an increasingly important role in safety. AI can automate threat detection and response. This helps security teams to be more proactive.
The Internet of Things (IoT) is expanding the attack surface. Securing IoT devices is a growing challenge. IoT safety requires a holistic approach.
Quantum computing poses a potential threat to current encryption methods. Post-quantum cryptography is an area of active research. Preparing for the quantum era is essential for long-term safety.