Cloud Computing Security
Imagine entrusting your most valuable possessions to a bank vault renowned for its state-of-the-art security. That’s essentially what cloud computing does with your data. But what happens when even the most secure vaults are targeted? Cloud computing has revolutionized how businesses operate, offering scalability, flexibility, and cost-effectiveness.
However, this digital transformation brings with it a critical concern: security. Cloud computing security refers to the policies, technologies, and controls that protect cloud-based systems, data, and infrastructure. With breaches becoming increasingly sophisticated, understanding the intricacies of securing your cloud environment is no longer optional; it’s a necessity.
This article will delve into the key aspects of cloud security, exploring common threats, best practices for mitigation, and the tools you can leverage to safeguard your data in the cloud, ensuring your digital vault remains impenetrable.
Unlocking Cloud Security: A Practical Guide
Cloud computing is revolutionizing how businesses operate, offering scalability and flexibility. However, with these benefits comes the crucial concern of security. Navigating cloud security can seem daunting, but understanding key principles is the first step toward protection.
This article dives deep into cloud security. We will explore diverse aspects. We aim to equip you with the knowledge to safeguard your data and applications in the cloud environment.
Our focus isn’t just on theory. It will also provide actionable steps. These steps you can use to build a robust cloud security posture. Let’s get started.
The transition to the cloud is inevitable for many organizations, but it is accompanied by critical security considerations. In this article, we will discuss the key components of securing your cloud environment.
Understanding the Cloud Security Landscape
Cloud security is unique. It shares some aspects with on-premises security. Cloud security also presents new challenges. These challenges include shared responsibility and evolving threat models.
A core idea is the shared responsibility model. The cloud provider secures the infrastructure itself. You, the user, are responsible for protecting your data and applications within that framework.
This model means understanding what your provider handles. It also means understanding what you need to manage yourself. Confusion can lead to security gaps.
Another challenge stems from rapidly changing technology. New cloud services appear regularly. Organizations must stay updated and adapt their security approaches accordingly.
Different models such as SaaS, PaaS, and IaaS all have different areas to protect. Identifying what cloud model you have chosen is paramount in creating your security perimeter.
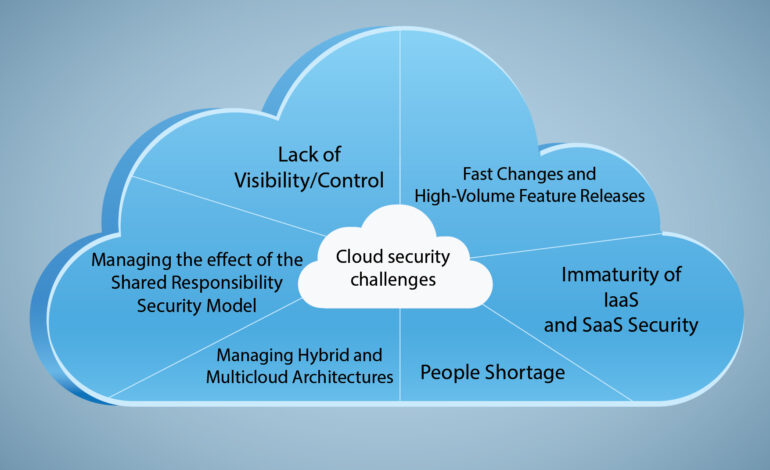
Key Cloud Security Concerns
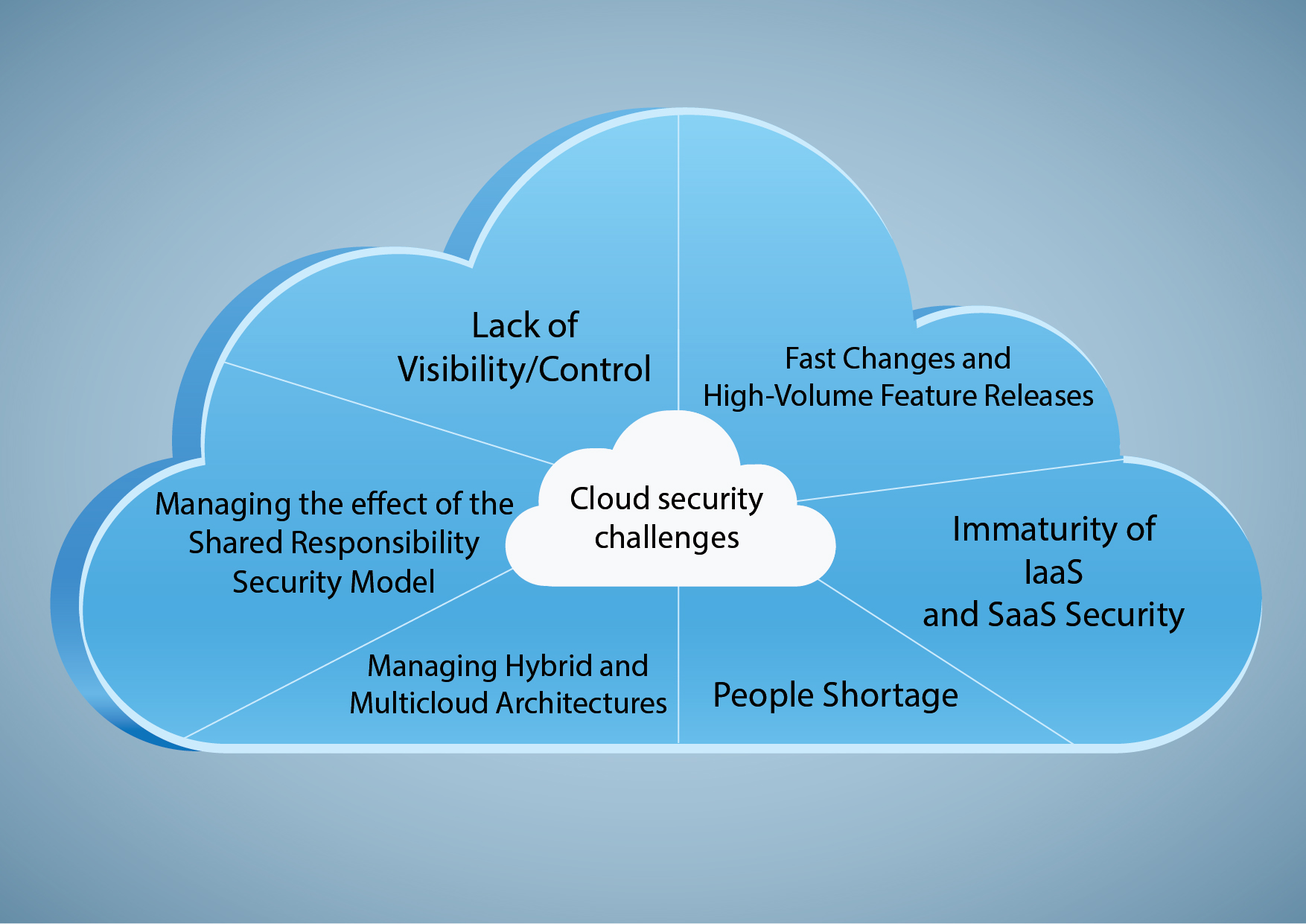
Data breaches are a primary concern in the cloud. Unauthorized access can expose sensitive information. Robust access controls and encryption are essential.
Misconfiguration is a common vulnerability. Leaving cloud services with default settings or incorrect permissions can create entry points for attackers. Regular audits are vital.
Identity and access management (IAM) is crucial. Enforcing strong passwords, multi-factor authentication, and the principle of least privilege can minimize risk.
Compliance is another factor. Regulations like GDPR and HIPAA impose specific security requirements for handling data in the cloud. Ensure your cloud setup meets these requirements.
Another critical concern is denial of service (DoS) attacks. These can disrupt access to cloud services. Implementing mitigation strategies can maintain availability.
Insider threats from employees or contractors are a major risk. A detailed policy and training program can help mitigate those types of incidents.
Implementing Cloud Security Best Practices
Start with a comprehensive risk assessment. Identify your assets, potential threats, and vulnerabilities. This assessment informs your security strategy.
Next, implement strong IAM controls. Limit access based on job role. Also, use multi-factor authentication. Regularly review user permissions.
Data encryption is vital, both in transit and at rest. Use strong encryption algorithms. Manage encryption keys securely.
Regularly monitor your cloud environment for suspicious activity. Use security information and event management (SIEM) tools to analyze logs and detect threats.
Implement a robust vulnerability management program. Regularly scan for vulnerabilities. Patch systems promptly.
Automate security tasks where possible. This reduces human error. It ensures consistent security practices.
Disaster recovery is also essential. Regular data backups and recovery plans can protect your business.
Train employees on cloud security best practices. Make sure they understand their role in maintaining security. Education is one of the strongest forms of defence.
Choosing the Right Cloud Security Tools
Many tools are available to enhance cloud security. Selecting the right ones depends on your specific needs and cloud environment.
Cloud access security brokers (CASBs) provide visibility and control over cloud applications. They can enforce security policies, prevent data leakage, and detect threats.
Firewall tools can help filter traffic coming into your cloud instances. This can also help isolate your cloud instance from the outside world.
Vulnerability scanners identify vulnerabilities in your cloud infrastructure. Patch management tools help you deploy security updates quickly.
SIEM tools aggregate logs from different sources. They help you detect and respond to security incidents. Choose tools that integrate with your cloud provider.
Data loss prevention (DLP) tools prevent sensitive data from leaving the cloud environment. This ensures compliance. It also reduces the risk of data breaches.
Endpoint detection and response (EDR) solutions protect individual devices that access cloud resources. This adds an extra layer of security.
The Future of Cloud Security
Cloud security is constantly evolving. Emerging technologies like AI and machine learning are playing a greater role.
AI-powered tools can automate threat detection. They can also improve incident response. Machine learning algorithms can identify anomalous behavior.
Zero trust security is gaining traction. It assumes that no user or device is inherently trustworthy. It requires strict verification for every access attempt.
Security automation and orchestration are becoming more important. They allow organizations to respond to threats more quickly and efficiently.
Staying informed about these trends is crucial for maintaining a strong cloud security posture. Prepare for future challenges.
As cloud environments grow in complexity, securing them will require a proactive and adaptive approach. Continuous learning is essential.