Cyber Security Software
Imagine waking up one morning to find your bank account drained, your social media accounts hijacked, and your personal information plastered across the internet. Sounds like a nightmare, right? Unfortunately, this is a reality for millions of people every year due to increasingly sophisticated cyber threats.
Cyber security software is the shield that protects you, your data, and your digital life from these very real dangers. It encompasses a wide array of tools and applications, from antivirus programs and firewalls to intrusion detection systems and data encryption software, all designed to identify, prevent, and respond to cyber attacks.
In this article, we’ll delve into the essential world of cyber security software, exploring its various types, key features to look for, and how to choose the right solutions to fortify your defenses in an ever-evolving digital landscape, empowering you to navigate the online world with confidence and peace of mind.
Navigating the Digital Fortress: A Deep Dive into Cyber Security Software
In today’s interconnected world, safeguarding your digital assets is more critical than ever. Cyber security software provides the shields needed to ward off a multitude of threats lurking in the digital shadows.
From individual users to huge corporations, everyone needs some protection. We’ll explore various types of cyber security solutions, helping you understand how they work and which ones are best suited for your specific needs.
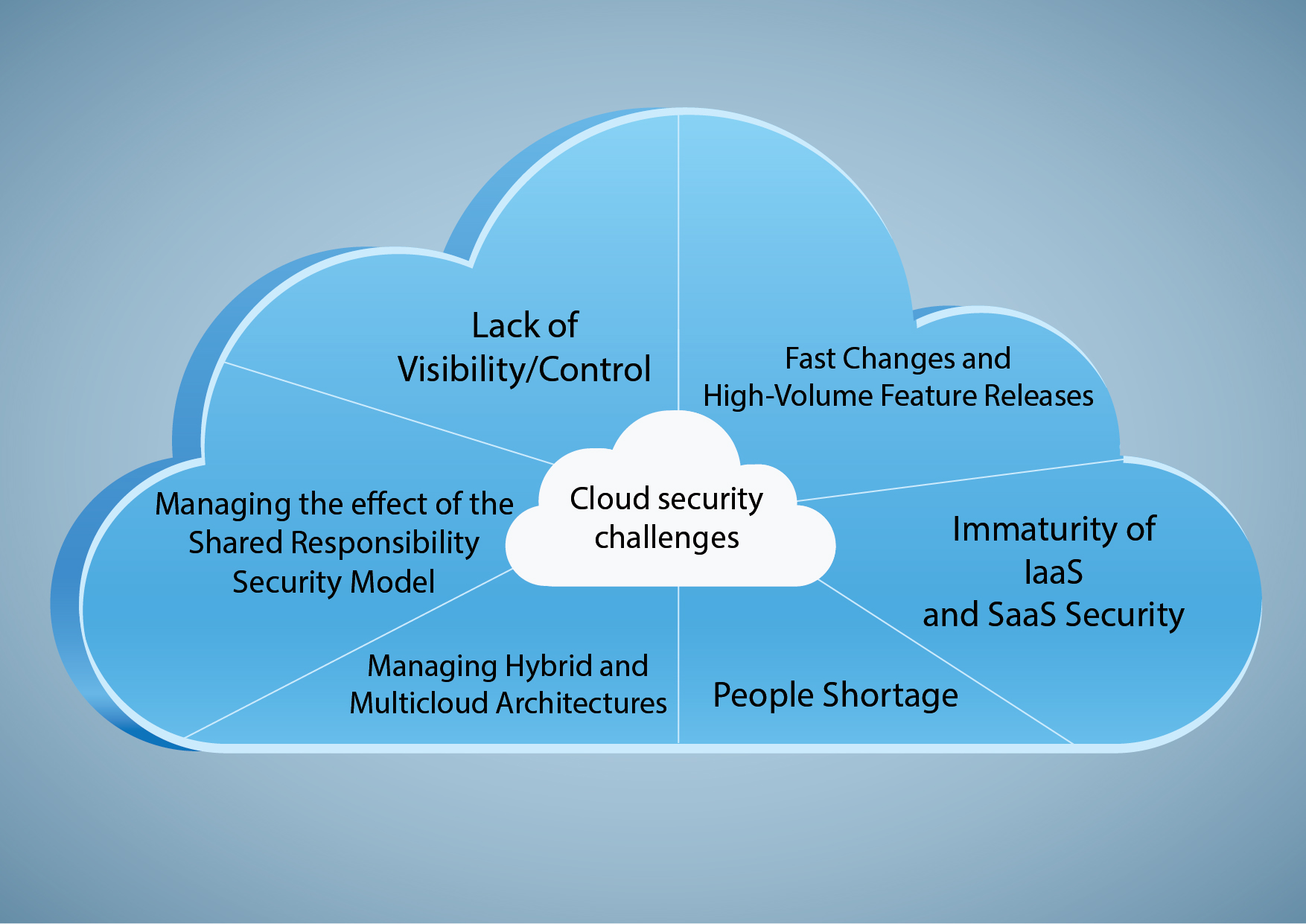
Understanding the Landscape of Cyber Threats
The cyber threat landscape is constantly evolving. Phishing attacks, malware, ransomware, and denial-of-service attacks are just a few of the challenges you might face, so preparedness is key.
Attackers are always developing innovative techniques, it requires diligence and a proactive security stance. Stay informed about current threats to stay a step ahead of potential danger.
Understanding common attack vectors enables you to implement more effective defenses and protect your data. Knowledge is power in the world of digital security.
Regularly updating your security protocols and software is vital in mitigating risks. This includes staying current with security patches and vulnerability disclosures.
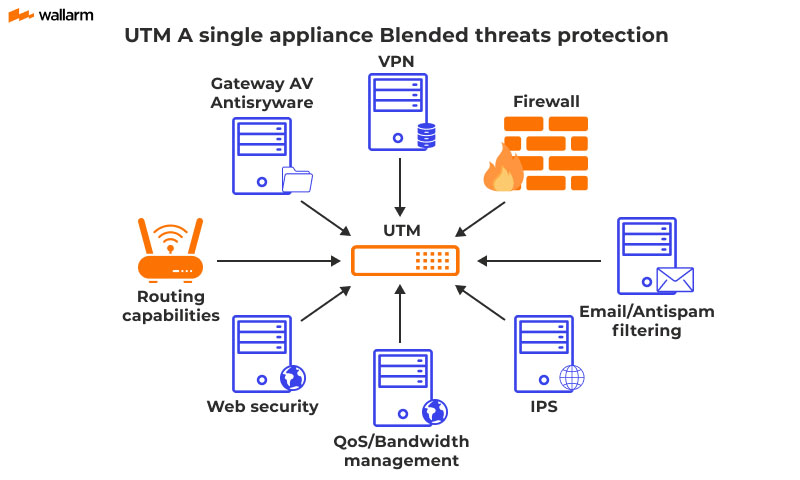
Essential Types of Cyber Security Software

Cyber security software comes in various forms. Antivirus programs, firewalls, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions all play vital roles.
Antivirus software scans your systems for malicious code, identifying and removing threats before they can cause harm. It’s the first line of defense for most users.
Firewalls act as barriers between your network and the outside world, controlling incoming and outgoing traffic. They block unauthorized access and potential attacks.
Intrusion detection systems (IDS) monitor network traffic for suspicious activity, alerting administrators to potential breaches. They provide a critical layer of surveillance.
Endpoint Detection and Response (EDR) solutions focus on monitoring and responding to threats on individual devices. They provide detailed insights and rapid incident response.
Choosing the Right Cyber Security Software
Selecting the appropriate cyber security software requires careful consideration. Factors like your specific needs, budget, and technical expertise should guide your decision-making.
Start by assessing your vulnerabilities and identifying the types of threats you are most likely to face. Understand your risk profile before making any investments.
Consider the scalability of the solution, ensuring it can grow with your needs. You don’t want to be constrained by the system you select as your requirements evolve.
Read reviews and seek recommendations from trusted sources before committing to a particular product. Real-world feedback can provide valuable insights. Furthermore, you might want to get a trial before you commit.
Ensure the software is compatible with your existing systems and infrastructure. Integration issues can lead to inefficiencies and security gaps.
Best Practices for Maintaining Cyber Security
Implementing cyber security software is only part of the equation. Ongoing maintenance and adherence to best practices are essential for sustained protection.
Regularly update your software and systems. Security patches often address critical vulnerabilities that attackers can exploit.
Educate yourself and your employees about cyber security threats and best practices. Human error remains a significant cause of data breaches.
Implement strong passwords and multi-factor authentication to protect your accounts. Strong authentication can prevent unauthorized access.
Conduct regular security audits to identify and address potential weaknesses. Proactive assessments can uncover vulnerabilities before they are exploited.