Firewalls And Network Security

Imagine your home without a front door, leaving everything inside vulnerable to anyone who walks by. That’s essentially what it’s like to operate online without robust network security. In today’s interconnected world, firewalls and network security are no longer optional extras; they’re the bedrock of protecting your data, devices, and entire digital life.
But what exactly is a firewall, and how does it stand guard against the ever-evolving threats lurking in the digital landscape? This article will demystify the world of firewalls and network security, explaining how they work, why they are absolutely crucial for individuals and businesses alike, and outlining the key steps you can take to fortify your digital defenses.
Get ready to learn practical strategies to safeguard your valuable information and navigate the internet with confidence.
Firewalls and Network Security: Protecting Your Digital Realm
In today’s digital landscape, network security is paramount. A robust defense strategy safeguards valuable data from a myriad of cyber threats. Firewalls play a crucial role, acting as the first line of defense against unauthorized access.
They are essential tools for individuals and organizations alike.
Think of a firewall like a bouncer at a nightclub, carefully scrutinizing who gets in. It examines incoming and outgoing network traffic based on a pre-defined set of rules. Any traffic that doesn’t meet the criteria gets blocked, preventing malicious actors from infiltrating your system.
Without a firewall, your network is essentially an open door for cybercriminals. They can access your personal information, steal sensitive business data, and wreak havoc on your systems. This could lead to financial loss, reputational damage, and legal repercussions.
It’s a risk simply not worth taking.
This article will delve into the intricacies of firewalls and network security, exploring different types of firewalls. You’ll learn how they work, why they’re so important, and how to choose the right one for your specific needs.
We’ll also cover related concepts like network segmentation and intrusion detection systems, providing a comprehensive overview of building a secure digital environment.
What is a Firewall?

A firewall is a network security system that monitors and controls incoming and outgoing network traffic. Its main function is to establish a barrier between a trusted internal network and an untrusted external network, such as the internet.
It acts as a gatekeeper, examining each packet of data and deciding whether to allow it through.
Firewalls operate based on a set of pre-configured rules, often referred to as access control lists (ACLs). These rules define what types of traffic are permitted or denied based on factors such as source and destination IP addresses, port numbers, and protocols.
If a packet matches a rule that denies access, the firewall blocks it.
The purpose of a firewall is to prevent unauthorized access to your network. Hackers often try to exploit vulnerabilities to gain entry. A firewall can prevent such attempts, filtering out harmful traffic and only permitting connections from trusted sources.
This protection extends to both incoming and outgoing communication, ensuring your data remains safe.
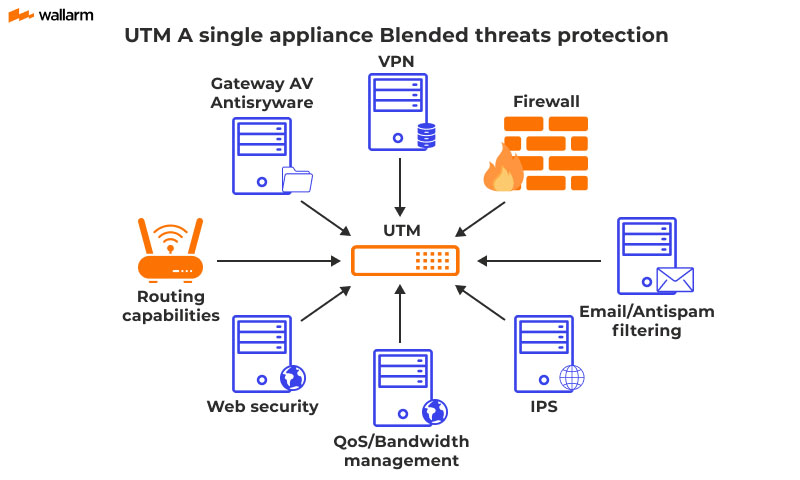
Modern firewalls are more sophisticated than their predecessors. Many incorporate advanced features like intrusion prevention, malware detection, and application control. These capabilities offer a multi-layered approach to security, ensuring that your network is protected from a wide range of threats.
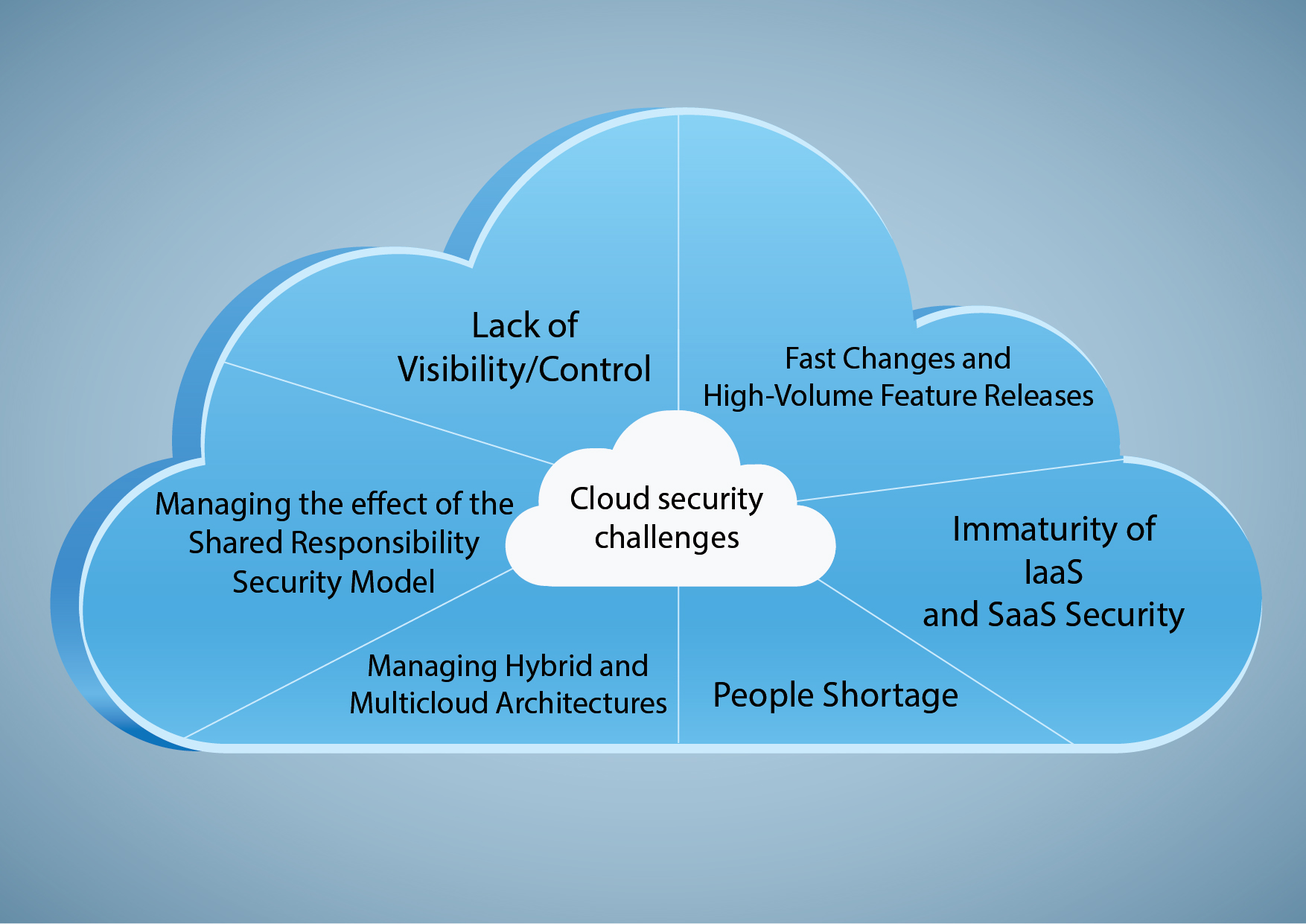
Types of Firewalls
Firewalls come in various forms, each designed with different capabilities. Understanding these types is essential when selecting the right firewall for your network. The main categories include packet filtering firewalls, stateful inspection firewalls, proxy firewalls, and next-generation firewalls.
Packet filtering firewalls are the most basic type. They examine individual packets of data and compare them against a set of rules. These firewalls are quick and simple but offer limited security. They don’t track the state of connections, making them vulnerable to certain types of attacks.
Stateful inspection firewalls offer a higher level of security. These firewalls track the state of active network connections, allowing them to make more informed decisions about whether to allow or deny traffic. They can identify and block malicious packets that would bypass a packet filtering firewall.
Proxy firewalls act as intermediaries between clients and servers. They intercept all network traffic and inspect it for malicious content. This provides a high level of security but can also impact network performance. Proxy firewalls are often used in environments where security is paramount.
Next-generation firewalls (NGFWs) incorporate a wide range of advanced security features, including intrusion prevention, application control, and malware detection. They provide a comprehensive security solution for modern networks. NGFWs are becoming increasingly popular as threats become more sophisticated.
The Importance of Network Segmentation
Network segmentation is the practice of dividing a network into smaller, isolated segments. Each segment acts as a separate network, limiting the impact of a security breach. If an attacker gains access to one segment, they won’t be able to access the entire network, preventing widespread damage.
Think of network segmentation like compartments in a ship. If one compartment is breached, the water doesn’t flood the entire ship. Instead, the damage is contained to that specific area. Similarly, network segmentation limits the scope of a security incident.
Implementing network segmentation involves creating virtual LANs (VLANs) or using physical separation. VLANs are logical subdivisions of a network that can be configured on network switches. Physical separation involves using separate physical networks for different parts of the organization.
Network segmentation can significantly improve your organization’s security posture. It reduces the attack surface, making it harder for attackers to gain access to sensitive data. It also allows you to implement different security policies for different segments, providing a more granular level of control.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are critical components of a comprehensive network security strategy. They work together to detect and respond to malicious activity on your network. While similar, they serve distinct purposes.
An IDS monitors network traffic for suspicious patterns and alerts administrators when it detects a potential threat. It’s like a security alarm that sounds when someone tries to break into your house. However, an IDS doesn’t actively block the threat; it simply notifies you of its presence.
An IPS, on the other hand, actively blocks malicious traffic and prevents attacks from succeeding. It’s like having a security guard who not only detects intruders but also stops them from entering your property. An IPS uses a variety of techniques to block attacks, including dropping malicious packets, resetting connections, and blocking IP addresses.
IDS and IPS systems often use signature-based detection, which relies on a database of known attack signatures. They also use anomaly-based detection, which identifies deviations from normal network behavior. This helps them detect zero-day attacks, which are attacks that haven’t been seen before.
By combining an IDS and IPS, you can create a robust defense against a wide range of cyber threats. The IDS will alert you to potential problems, and the IPS will actively block attacks, keeping your network safe and secure.
These systems should always be configured and actively monitored by IT professionals.