Network Security In Computer Network
In today’s hyper-connected world, consider this: a cyberattack occurs approximately every 39 seconds. This alarming statistic underscores the critical importance of network security in our increasingly digital lives. But what exactly is network security in the context of a computer network? Simply put, it’s the practice of protecting your network and its data from unauthorized access, misuse, and attacks.
Think of it as the digital fortress safeguarding your valuable information, whether you’re a home user streaming movies or a global corporation managing sensitive data. Without robust network security measures, you risk data breaches, financial losses, reputational damage, and a host of other serious consequences.
This article will delve into the key aspects of network security, exploring common threats, essential security tools and techniques, and best practices for building a strong defense against cyberattacks. By understanding these concepts, you’ll be better equipped to protect your network and the valuable data it carries, ensuring a safer and more secure digital experience.
Network Security in Computer Networks: A Comprehensive Guide
In today’s interconnected world, safeguarding data flowing across computer networks is paramount. Network security encompasses the policies, procedures, and technologies implemented to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and its accessible resources.
Think of it like this: your network is a house. You need locks (passwords), an alarm system (firewall), and maybe even security cameras (intrusion detection systems) to keep the bad guys out and your precious data safe inside.
This article will explore the vital aspects of network security, including the core concepts, common threats, and proactive measures to protect your digital assets. We’ll break down the jargon and provide a practical understanding of securing your network.
Ultimately, a robust network security strategy is essential for maintaining confidentiality, integrity, and availability of information, fostering trust, and ensuring business continuity. Ignoring it is like leaving your front door wide open to anyone who wants to walk in.
Understanding the Core Principles of Network Security
Network security rests on three pillars: confidentiality, integrity, and availability – often referred to as the CIA triad. These principles guide the design and implementation of security measures to protect data.
Confidentiality ensures that information is accessible only to authorized individuals. Encryption, access controls, and data masking are some of the techniques employed to maintain confidentiality.
Integrity safeguards the accuracy and completeness of data, preventing unauthorized modification or deletion. Hash functions, digital signatures, and version control are crucial for data integrity.
Availability guarantees that authorized users can access information and resources when needed. Redundancy, backups, and disaster recovery plans are essential for ensuring availability, even during outages.
These principles form the foundation of a secure network. A weakness in any one area can compromise the entire system. It’s about creating a layered defense, similar to having multiple locks on your door.
Think of confidentiality as whispering a secret; integrity as ensuring the secret stays the same; and availability as being able to tell the secret whenever you need to.
Common Network Security Threats and Vulnerabilities
The digital landscape is rife with threats that can compromise network security. Recognizing these threats is the first step in defending against them. Understanding how they work is critical.
Malware, including viruses, worms, and Trojans, can infiltrate networks to steal data, disrupt operations, or gain unauthorized access. It is like a contagious disease spreading through your network.
Phishing attacks deceive users into divulging sensitive information through fraudulent emails or websites. These are the con artists of the digital world, trying to trick you into giving up your secrets.
Denial-of-service (DoS) attacks overwhelm a network with traffic, rendering it unavailable to legitimate users. Imagine a flood of people trying to enter a building at once, blocking the doorway.
Man-in-the-middle attacks intercept communication between two parties, allowing attackers to eavesdrop or tamper with data. This is like having someone secretly listening in on your phone calls.
Unpatched software vulnerabilities and weak passwords create openings for attackers to exploit. Think of these as unlocked windows or weak spots in your armor.
Insider threats, originating from within an organization, can be especially difficult to detect and prevent. A disgruntled employee could intentionally sabotage the network.
Implementing Effective Network Security Measures
Protecting your network requires a multi-layered approach, encompassing various security measures. There’s no single “silver bullet;” it’s about creating a comprehensive defense system.
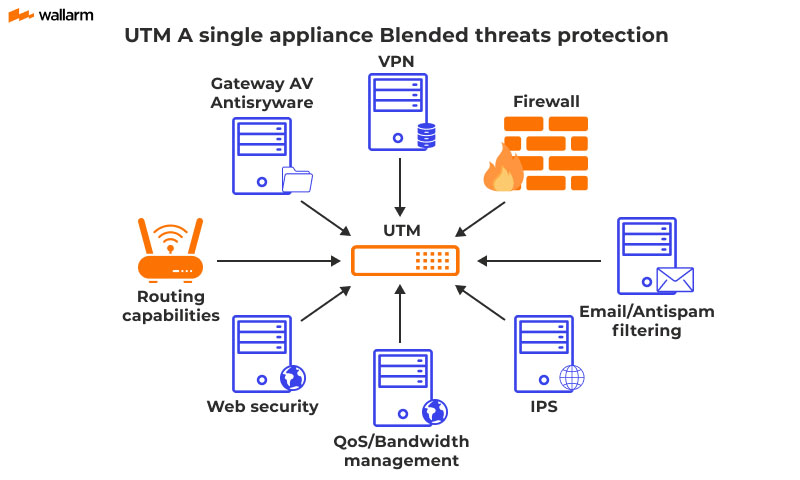
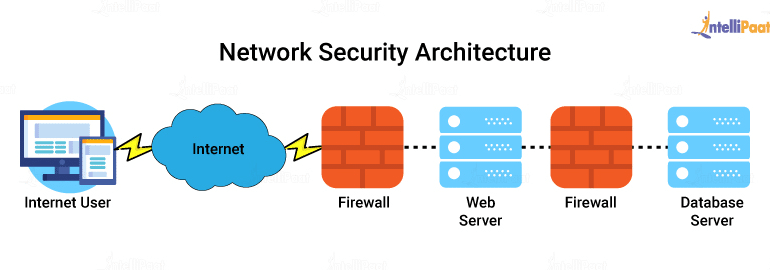
Firewalls act as barriers, controlling network traffic based on predefined rules, blocking unauthorized access attempts. They are the gatekeepers of your network, deciding who gets in and who doesn’t.
Intrusion Detection and Prevention Systems (IDS/IPS) monitor network traffic for malicious activity, alerting administrators and automatically blocking suspicious traffic. They are your network’s security cameras and alarm system.
Virtual Private Networks (VPNs) create secure tunnels for transmitting data over public networks, encrypting traffic and protecting it from eavesdropping. Think of it as a private, encrypted highway for your data.
Strong passwords and multi-factor authentication (MFA) add layers of security, making it more difficult for attackers to gain unauthorized access. A strong password is like a complex combination lock, while MFA is like requiring two keys to open the door.
Regular software updates and patching address known vulnerabilities, closing potential entry points for attackers. Keeping your software up-to-date is like fixing the holes in your roof before the rain comes.
Employee training and awareness programs educate users about security threats and best practices, reducing the risk of human error. A well-informed workforce is your first line of defense.
Network segmentation divides the network into smaller, isolated segments, limiting the impact of a security breach. This is like having separate rooms in your house; if one room is compromised, the rest remain safe.
The Importance of Regular Security Audits and Monitoring
Network security is not a one-time effort; it requires ongoing monitoring and adaptation. Continuous vigilance is key to staying ahead of emerging threats.
Regular security audits assess the effectiveness of existing security measures, identifying vulnerabilities and recommending improvements. Consider it a health checkup for your network.
Vulnerability scanning tools automatically scan networks for known vulnerabilities, providing insights into potential weaknesses. This helps to identify areas that need immediate attention.
Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources, providing real-time threat detection and alerting. SIEM is like having a central security command center for your network.
Continuous monitoring of network traffic and system activity can help detect anomalies and potential security breaches. Early detection is crucial for minimizing the impact of a successful attack.
Incident response plans outline the steps to be taken in the event of a security breach, ensuring a coordinated and effective response. Having a plan in place allows you to react quickly and efficiently.
By proactively monitoring and adapting your security posture, you can minimize risk and protect your network against evolving threats. Think of it as constantly adjusting your sails to navigate the changing winds.