Unified Threat Management Software
Imagine your business network as a fortress under constant siege. Viruses, malware, phishing attacks, and intrusion attempts are the relentless enemies trying to breach your defenses. Managing each threat individually, with a separate security solution, is like fighting with one hand tied behind your back.
This is where Unified Threat Management (UTM) software comes in, acting as a centralized security command center. UTM solutions consolidate essential security features – firewall, intrusion detection/prevention, antivirus, anti-spam, VPN, and web filtering – into a single, integrated platform.
In essence, it’s a comprehensive security system designed to simplify network protection and improve overall security posture. This article will delve into the specifics of UTM software, exploring its benefits, key features, and how it can streamline your cybersecurity efforts to keep your digital fortress secure and your business thriving.
Get ready to discover how UTM can be your organization’s best defense against the ever-evolving threat landscape.
Understanding Unified Threat Management (UTM) Software
In today’s complicated digital landscape, shielding your network from diverse dangers can seem like a never-ending task. That’s where Unified Threat Management (UTM) comes into play, acting as a comprehensive security solution.
UTM is fundamentally a single security appliance that combines several security functions into one. This simplifies administration and delivers better protection against a variety of attacks.
Imagine a Swiss Army knife, but for cybersecurity. It’s designed to offer centralized protection for your entire network, simplifying security management while improving defense.
Think of UTM as your network’s all-in-one bodyguard, constantly watching for danger and prepared to neutralize threats before they can harm your systems. A UTM solution provides an effective defense against a wide range of digital dangers.
Key Components of a UTM System
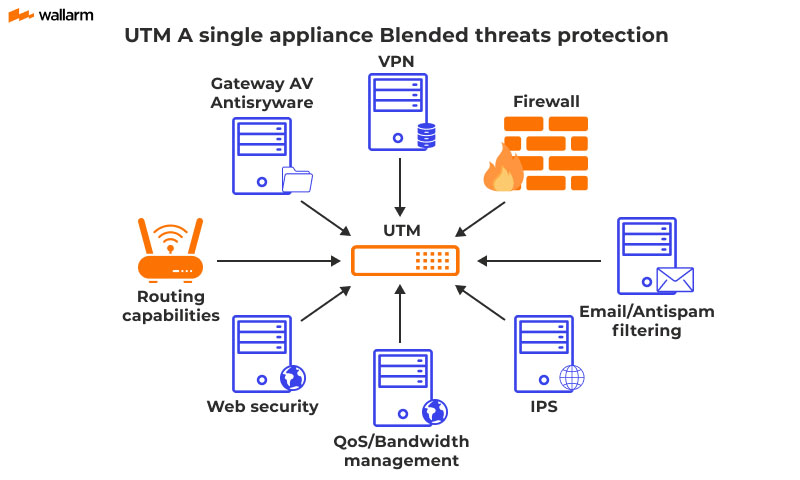
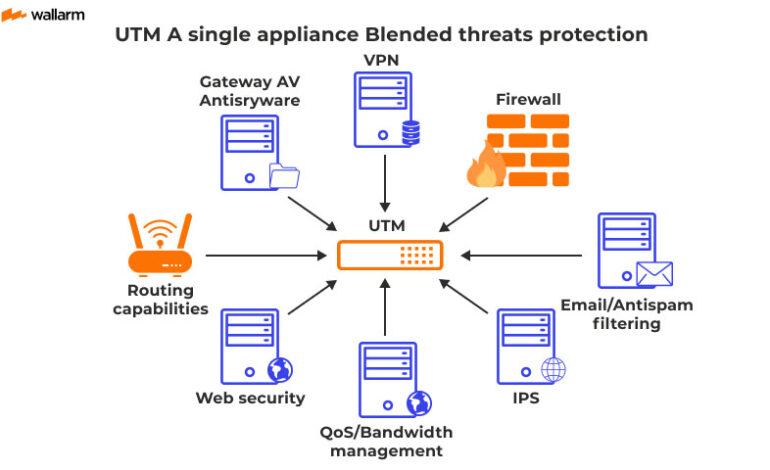
A good UTM blends several critical security functions. These components work synergistically to deliver robust network protection.
Firewall: The firewall serves as the first line of defense. It monitors network traffic and blocks any unauthorized access, maintaining a crucial barrier.
Intrusion Detection and Prevention (IDS/IPS): These systems analyze network traffic for malicious activity. They detect and block or prevent potential intrusions in real-time.
Antivirus: The antivirus scans files and network traffic for viruses and malware. It cleans or quarantines infected files to prevent spread, keeping your system safe.
VPN Support: Virtual Private Network (VPN) provides secure, encrypted connections. It enables remote users to securely access the network, and it secures communication between sites.
Web Filtering: This feature controls website access, preventing users from visiting risky or unproductive sites. It assists in compliance and prevents malware downloads, ensuring a secure browsing environment.
Spam Filtering: This component blocks unwanted email, reducing the risk of phishing attacks and malware delivery through email. It keeps inboxes clean and reduces security dangers.
Benefits of Implementing UTM
Employing UTM software can radically improve your organization’s security posture and streamline IT management. It offers a more convenient, effective and powerful approach to cybersecurity.
Simplified Management: Handling several security tools can be complex. UTM centralizes management, making it easier to configure and monitor security policies. This simplifies the life of IT professionals.
Reduced Costs: Buying separate security solutions can be expensive. A UTM combines these functions into a single appliance, saving money on hardware, software, and maintenance.
Improved Security: UTM solutions provide a comprehensive security approach. They protect against a wide range of threats with integrated features, enhancing overall security.
Enhanced Performance: Dedicated security appliances can slow down network performance. UTM systems are built to optimize security functions without sacrificing speed, giving faster and seamless operation.
Better Visibility: UTM solutions provide centralized reporting and monitoring capabilities. This gives enhanced visibility into network security events, aiding in rapid threat detection and response.
Choosing the Right UTM Solution
Selecting the appropriate UTM solution for your organization necessitates careful consideration of your specific needs and requirements. Not all UTM solutions are created equal.
Assess Your Needs: Define your organization’s security needs and budget. Understand the size of your network, the number of users, and the types of data you need to protect.
Evaluate Features: Assess the features provided by each UTM solution. Ensure it includes all the essential components, such as firewall, IDS/IPS, antivirus, and web filtering.
Consider Scalability: Select a UTM solution that can scale with your business growth. It should be able to handle increased network traffic and an expanding user base.
Check for Integration: Make sure the UTM solution can integrate with your existing IT infrastructure. It should work seamlessly with your current hardware, software, and cloud services.
Read Reviews: Explore reviews and testimonials from other users. This can provide insights into the performance, reliability, and ease of use of different UTM solutions.